Get FREE expert insights and resources for your business and career - in whatever format you prefer.
Download templates, get access to tools, hear podcasts, and learn from our experts. Find just the right business-moving and career-building resources to suit your learning style. Looking for help with something else? Contact us ❯
Expert Led Cybersecurity Research
Are your passwords in the green?
See how fast your password could be cracked with the 2025 Hive Systems Password Table, built using real-world hardware benchmarks and attack methods. Use it to reinforce strong password policies and support awareness training with hard data.
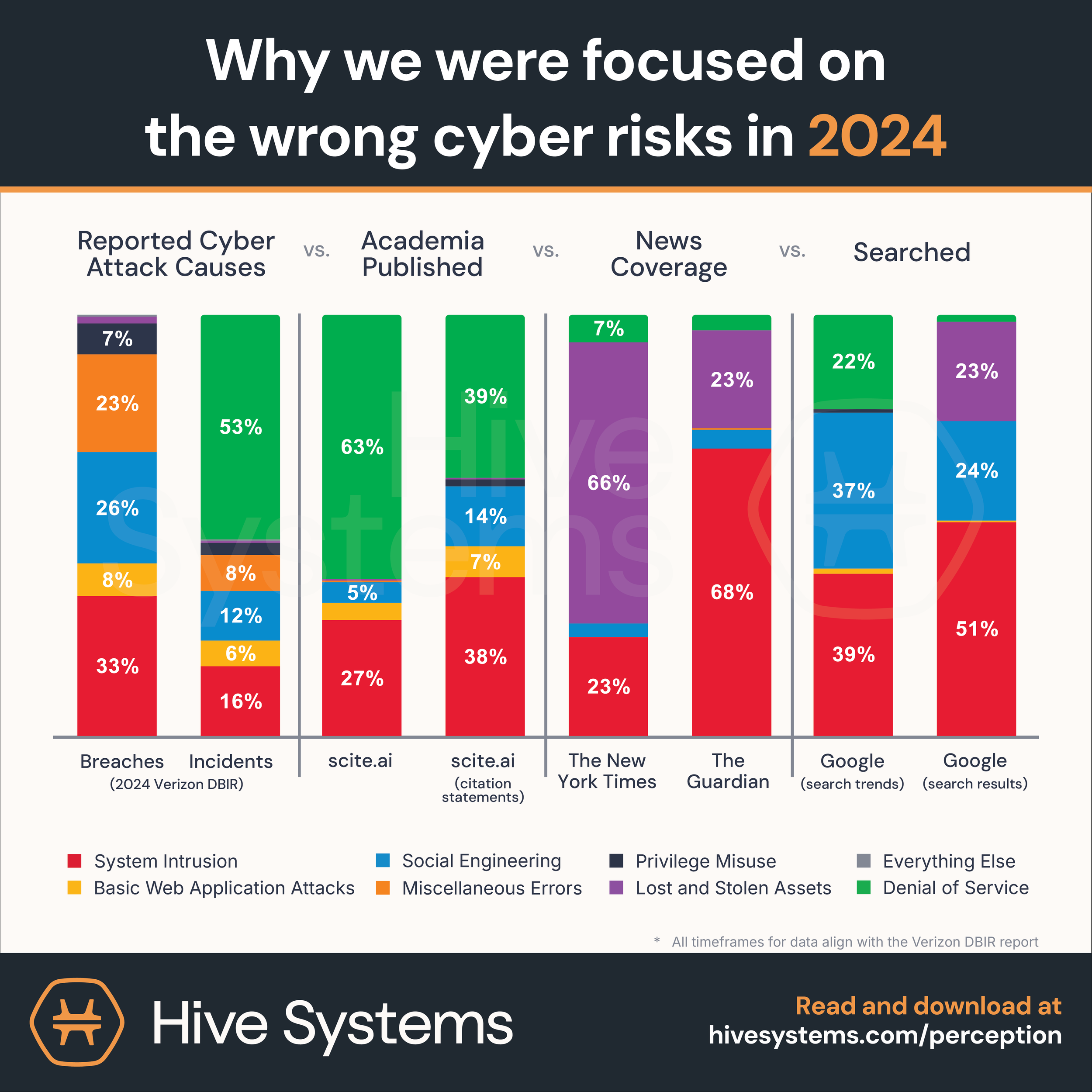
Is your company focused on the wrong risks?
Understand where public opinion diverges from actual threats with our Cyber Attack Perceptions in 2025 chart, which compares real-world attack causes to media coverage and search trends. It’s the visual you need to shift conversations and guide smarter cybersecurity priorities.
Expert Developed Guides and Tools
Start measuring your cyber risk in dollars.
The Quantitative Cyber Risk Assessment Tool lets you model probable threats and financial impact, giving you a data-driven snapshot of your exposure. It’s a quick way to bring clarity and credibility to risk discussions. Need more power? Then check out Derive - our leading data drive cybersecurity operations and risk management platform
Launch your cybersecurity program today.
Use the Cybersecurity Program Accelerator Kit to access foundational tools - policy templates, risk checklists, awareness assets -to jumpstart your cybersecurity program. Perfect for teams launching or scaling their cybersecurity efforts.
Boost awareness with tubular posters.
The Phishing Awareness Posters pack delivers playful, “90’s nostalgia” artwork designed to catch attention and reinforce secure behavior. Hang them at desks or break rooms to keep phishing awareness front and center.
Secure your social media accounts.
Follow the Social Media Security Guide to lock down personal and business accounts across platforms like LinkedIn, X, Facebook, Instagram, and YouTube. Great for reputational protection and decreasing exposure to social engineering.
Bridge HIPAA with NIST CSF.
The HIPAA to NIST CSF v1.1 Mapping Guide helps healthcare organizations translate HIPAA Security Rule requirements into NIST Cybersecurity Framework language. It’s the precise reference you need for alignment and audit prep.
Keep awareness visible and professional.
The Business Booster Poster Pack delivers clean, office-ready designs that reinforce phishing best practices without breaking your brand aesthetic. Perfect for executive spaces and hybrid teams.
Get clickers thinking twice.
The Allied Advertising Poster Pack uses bold, 1940’s visuals and sharp copy to land security messages fast. Great for catching attention in hallways, break rooms, and inboxes - especially for companies in the Defense Industrial Base.
Expert Created Cybersecurity Content
Hear what’s shaping cybersecurity next.
The Hive Live Podcast features expert interviews, fresh perspectives, and real-world stories from across the cybersecurity landscape. Tune in to hear what matters - and what’s coming next.
Make sense of cybersecurity threats without the jargon.
The Approachable Cyber Threats (ACT) Blog breaks down risks, headlines, and industry trends into clear, actionable insights. Written by our team to keep you informed, not overwhelmed.
Expert Built CMMC Resources
Understand where you stand.
Access our FREE CMMC Level 2 Assessment Tool to complete your CMMC Level 2 self assessment. Our free tool will walk you through all the criteria for your assessment to obtain your CMMC-required SPRS score and identify gaps and areas for improvement prior to engaging a C3PAO.
Jump start your paperwork.
Our comprehensive CMMC SSP templates to help you build your CMMC-compliant System Security Plan (SSP) using NIST 800-171 Rev. 2, or prepare for the future with NIST 800-171 Rev. 3.
Looking for a CMMC deep dive?
Our expert-written CMMC 101 Guide helps you understand the history of the Cybersecurity Maturity Model Certification (CMMC) and navigate its requirements in an approachable way.
CMMC Blog Posts
Our Approachable Cyber Threats (ACT) blog is the best place for the latest cybersecurity information, including CMMC. Check out our curated list of CMMC focused posts!
CMMC Podcast Episodes
Our Hive Live podcast is the best place for the in depth analysis and discussion about the latest cybersecurity information, including CMMC. Check out our curated list of CMMC focused episodes!
How do I sell CMMC to my leadership?
Get tips and tricks for making the case for CMMC to your leadership - showing how compliance protects revenue, reduces risk, and creates a competitive advantage in the Defense Industrial Base.
Why a C3PAO Assessment?
Strengthen your competitive edge with our guide for selling your leadership on a C3PAO assessment - unlocking new DoD contract opportunities, reducing compliance burdens, and ensuring expert-validated cybersecurity readiness.
Not all C3PAOs are created equal.
Our CMMC C3PAO Guide breaks down what to look for (and what to avoid) when choosing a Certified Third Party Assessment Organization for your CMMC assessment - so you can move forward with confidence.
What’s the fastest path to CMMC Level 2?
Get a clear, month-by-month plan for reaching CMMC Level 2. This guide breaks down every major milestone - with templates, practical advice, and expert insight built around what C3PAO assessors actually look for. Whether you’re starting from scratch or catching up, this roadmap helps you get ready faster, with fewer surprises.