CMMC Is Here: Your Essential Guide to Identifying and Protecting Federal Contract Information (FCI)
Category
CMMC, Guides
Risk Level
As the CMMC program takes effect, understanding what qualifies as Federal Contract Information (FCI) is critical. This guide breaks down FCI definitions, offers practical tips for identifying and handling FCI across your organization, and walks you through applying CMMC Level 1 controls—ensuring you stay compliant, secure, and ready for the new era of defense contracting.
The Cybersecurity Maturity Model Certification (CMMC) Program is officially in effect as of December 16th, 2024. Defense contractors and their subcontractors must ensure they understand what Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) are so they can adequately protect the data on their systems. While there are many resources out there that dive into CUI, including the CUI Registry, there is very little explicit guidance on FCI.
“What is FCI?”
The official definition of FCI from FAR 52.204-21 states that FCI is “information, not intended for public release, that is provided by or generated for the Government under a contract to develop or deliver a product or service to the Government, but not including information provided by the Government to the public, such as that on public Web sites, or simple transactional information, such as that necessary to process payments.” Talk about a long definition! Let’s break out the individual parts:
Not intended for public release: It doesn’t get simpler than that. If the information you’re looking at is going to the public, it’s not FCI.
Provided by the Government: If the Government is providing it directly to your company, and you’ve already confirmed the information is not intended for the public, it may be FCI.
Generated for the Government: If your company or a subcontractor has created the information, and that information is being provided to the Government, then it may be FCI.
Under a contract to develop or deliver a product or service to the Government: This part is the key to this whole definition. We are only looking at information that pertains to a contract. If the information is provided by the Government, but it’s not related to the contract, then it’s not FCI (though it may be subject to other handling or distribution rules, so make sure you’re paying attention to any labels or document controls on information you receive from the Government). The same goes for information generated for the Government - if the information is being provided to the Government, but was not part of a contract to deliver goods or services to the Government, then it is not FCI.
Not simple transactional information, such as that necessary to process payments: Bank details, such as the account and routing numbers used to receive payments, are not FCI.
“That’s a lot to unpack. How do I figure out what data is FCI in my environment?”
The gateway to FCI is the contract, so that’s the best place to start. Collect your contracts from the Government and see what activities fall under those contracts. If you’re a subcontractor and the Prime has flowed Government contracts down to you, or has noted that the work performed under that contract is considered FCI, include those activities as well. Now that you’ve collected that information, ask yourself:
Was the information related to this contract provided by the Government?
Was the information related to this contract generated for the Government?
Is the information not intended for public release?
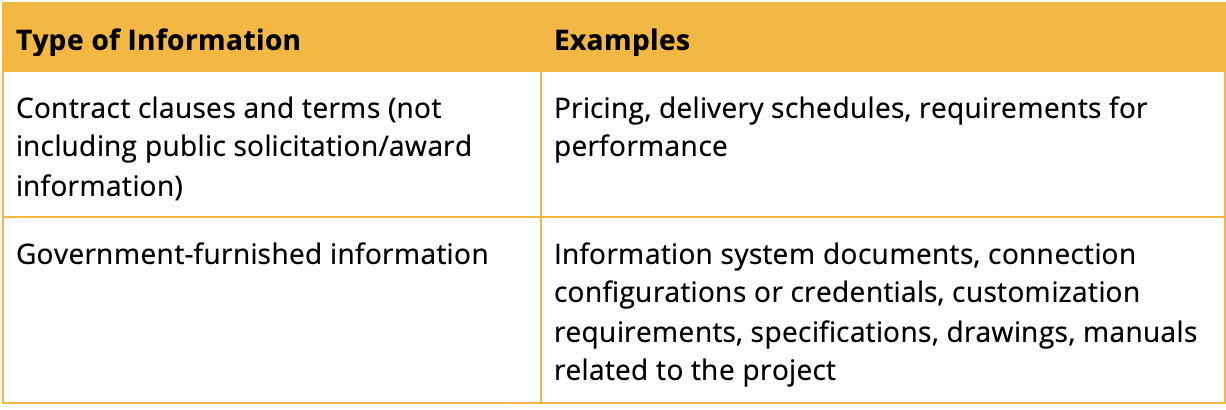
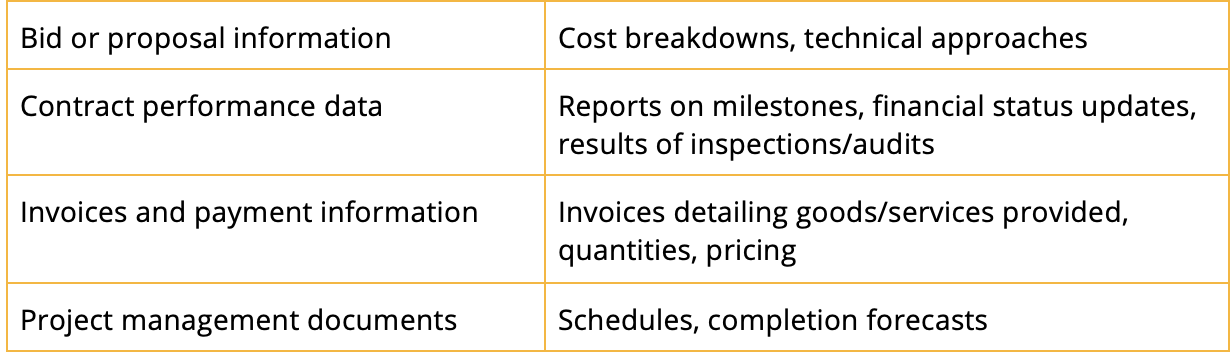
If you answered “yes” to any of these questions, the information is FCI. Some common examples of FCI include:
“Now that I know what data is FCI, how do I make sure I’m meeting CMMC requirements?”
Follow the flow of the information to determine your scope. On the bright side, CMMC Level 1 is simple. If the asset processes, stores, or transmits FCI then it’s in scope; if it doesn’t, then it’s out of scope. Does your sales team receive contract information via email and store it in a CRM tool? The sales team personnel, email, and CRM tool are all FCI assets and must be secured with all 17 CMMC Level 1 controls. Are you providing a service to the Government where your employees log into an enclave to provide work, and the team project manager updates all project management documentation, sends it via email, and provides updates in status meetings? The project team personnel, project manager, VDI environment, project manager’s endpoint, email, and virtual meeting solution are all FCI assets. It is critical to identify data flows to ensure you are considering all possible FCI assets, securing them in accordance with CMMC Level 1 requirements, and validating ongoing compliance through annual self-assessments.
Still not sure if you’ve accounted for all your FCI? Hive Systems is here to help! Our team has Certified CMMC Assessors and Certified CMMC Professionals who are well-versed in NIST 800-171 requirements, the CMMC assessment methodology, and various solutions to meet your unique CMMC needs.
Follow us - stay ahead.