Your Guide to Engaging with a C3PAO
CMMC is here and C3PAO assessments began on January 2, 2025. So what should you expect from an assessment, and how can you set your company up for success?
CMMC Is Here: Your Essential Guide to Identifying and Protecting Federal Contract Information (FCI)
As the CMMC program takes effect, understanding what qualifies as Federal Contract Information (FCI) is critical. This guide breaks down FCI definitions, offers practical tips for identifying and handling FCI across your organization, and walks you through applying CMMC Level 1 controls—ensuring you stay compliant, secure, and ready for the new era of defense contracting.
Approachable CMMC: Accelerate with our SSP Template
Are you part of the Defense Industrial Base (DIB) or have Department of Defense (DoD) contracts? Then your deadline for implementing the Cybersecurity Maturity Model Certification (CMMC) 2.0 requirements is fast approaching.
Who is Watching You and Why?
In the musical words of Rockwell, 🎵 “I always feel like somebody’s watching me - and I have no privacy.” 🎵Who might be watching you through your webcam, and what can you do to stop it?
Passkey to the (Passwordless) Future
What would it be like to live in a world without having to memorize and type a million of passwords? Logging in without having to enter a password has been practically impossible - until now.
Data Breach 101: Actions to Take After a Breach
Data breaches are a significant concern here in the digital age. With technology advancing rapidly, hackers have been using various methods to gain sensitive information from unsuspecting individuals, organizations, and you.
#Secure: Locking Down Your Social Media in Style
Social media platforms are essential tools for personal and professional communication. The increasing number of cyber threats means protecting your accounts has become paramount.
Keep Calm and Check Your Public Wi-Fi Connection
When it comes to public Wi-Fi, it is “better to be safe than sorry.” Read our guide and secure your Wi-Fi connection when you travel.
Let’s Not Get Smished
Email isn't the only way hackers try to get your information. They can also use text messages to entice victims to click on links in scams known as “smishing.”
Whitepaper: The Intersection of Technical Debt and Cybersecurity
Understanding the impact of technical debt on your business operations and cybersecurity efforts can be a challenge. That’s why Hive Systems and BARR Advisory partnered on an in-depth whitepaper to explore how organizations can recognize, prevent, and manage technical debt.
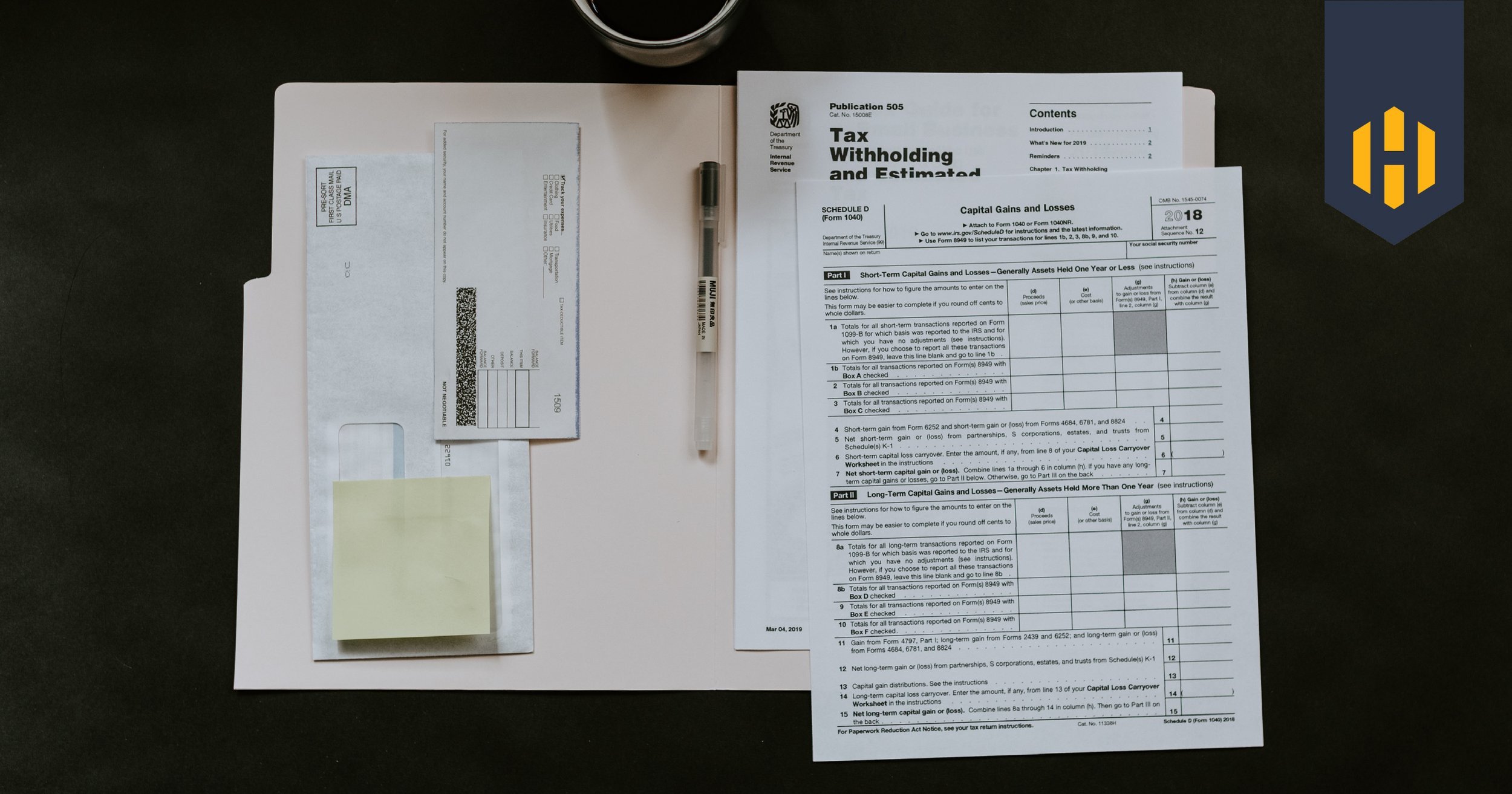
Avoiding Tax Scams in 2022
Last week, millions of Americans finalized their tax returns. Tax Day, however, isn’t the final day for scammers who are interested in harvesting your personal financial information. Here are some of the scams we see most frequently, and some tips for avoiding them.
What’s an IT Budget and How Much Should I Spend on Cybersecurity?
We break down the steps to proper IT budgeting that will keep your company in business.
A Guide to Increasing Your Email Security and Deliverability: DMARC
Your misconfigured email can send your emails to spam inboxes and let hackers pretend to be you - costing you millions. In part 3 of this guide, we’ll pull everything from the first two parts together and cover DMARC.
A Guide to Increasing Your Email Security and Deliverability: DKIM
Your misconfigured email can send your emails to spam inboxes and let hackers pretend to be you - costing you millions. In part 2 of this guide, we’ll cover configuring DKIM records.
A Guide to Increasing Your Email Security and Deliverability: SPF
Your misconfigured email can send your emails to spam inboxes and let hackers pretend to be you - costing you millions. In part 1 of this guide, we’ll cover configuring your SPF record.
Let’s Go Phishing
How a simple phishing email will shut down your company if you’re not careful.
Let's Talk About Cybersecurity in 2020 by the Numbers
Let's talk about Cybersecurity by the numbers from last year!
Let’s Talk About Password Managers!
Password managers are the most important way to secure your digital identity.