The Cyber Attack Perception Problem
Uncover the truth about cyber attack misconceptions with Hive Systems' latest research. Learn how media coverage skews public perception of cyber attacks and discover the real risks organizations face. Explore data-driven insights to better protect your business in an evolving threat landscape
Are Your Passwords in the Green?
It's the 2024 update to our Hive Systems Password Table - including using a new “most-hacked” password hash. See why our Password Table has been shown and written about on the news, published by universities, and shared by companies across the globe. Learn more and download your copy!
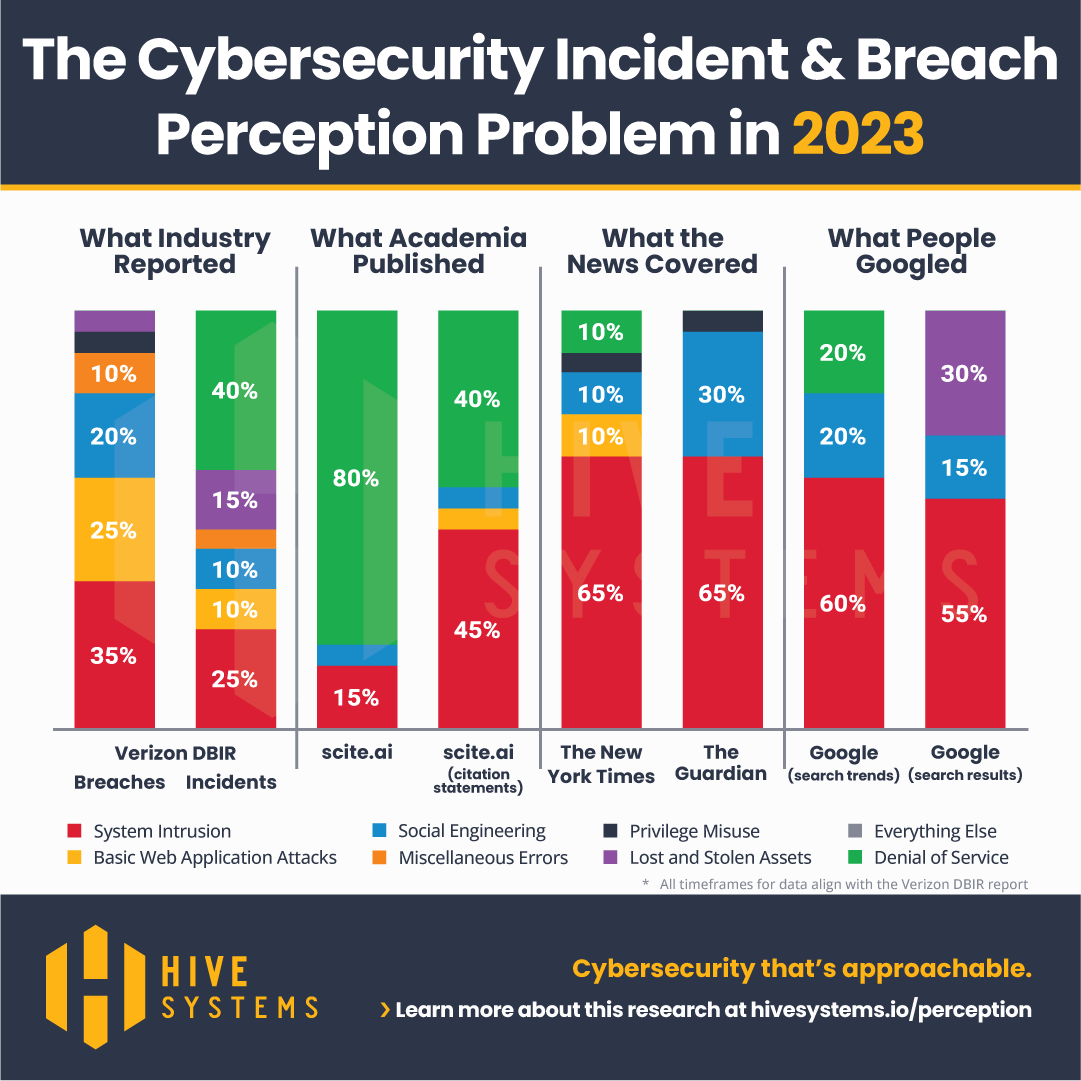
The Cyber Attack Perception Problem in 2023
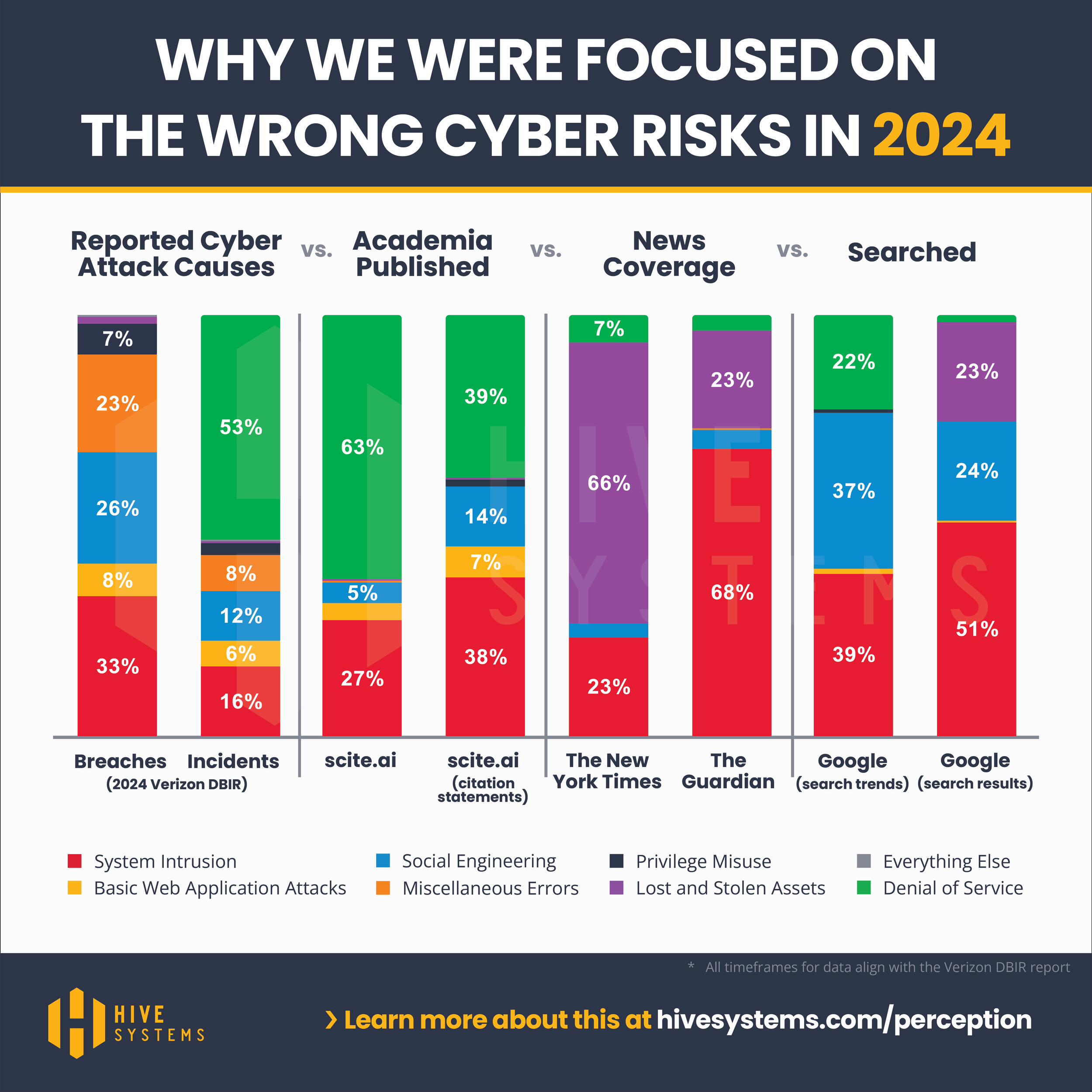
The 2023 update to our research that compares how cybersecurity incidents and data breaches occurred, what academia published, what the news covered, and what people Googled. So what’s new this year, what was our methodology, and what was surprising? Read on!
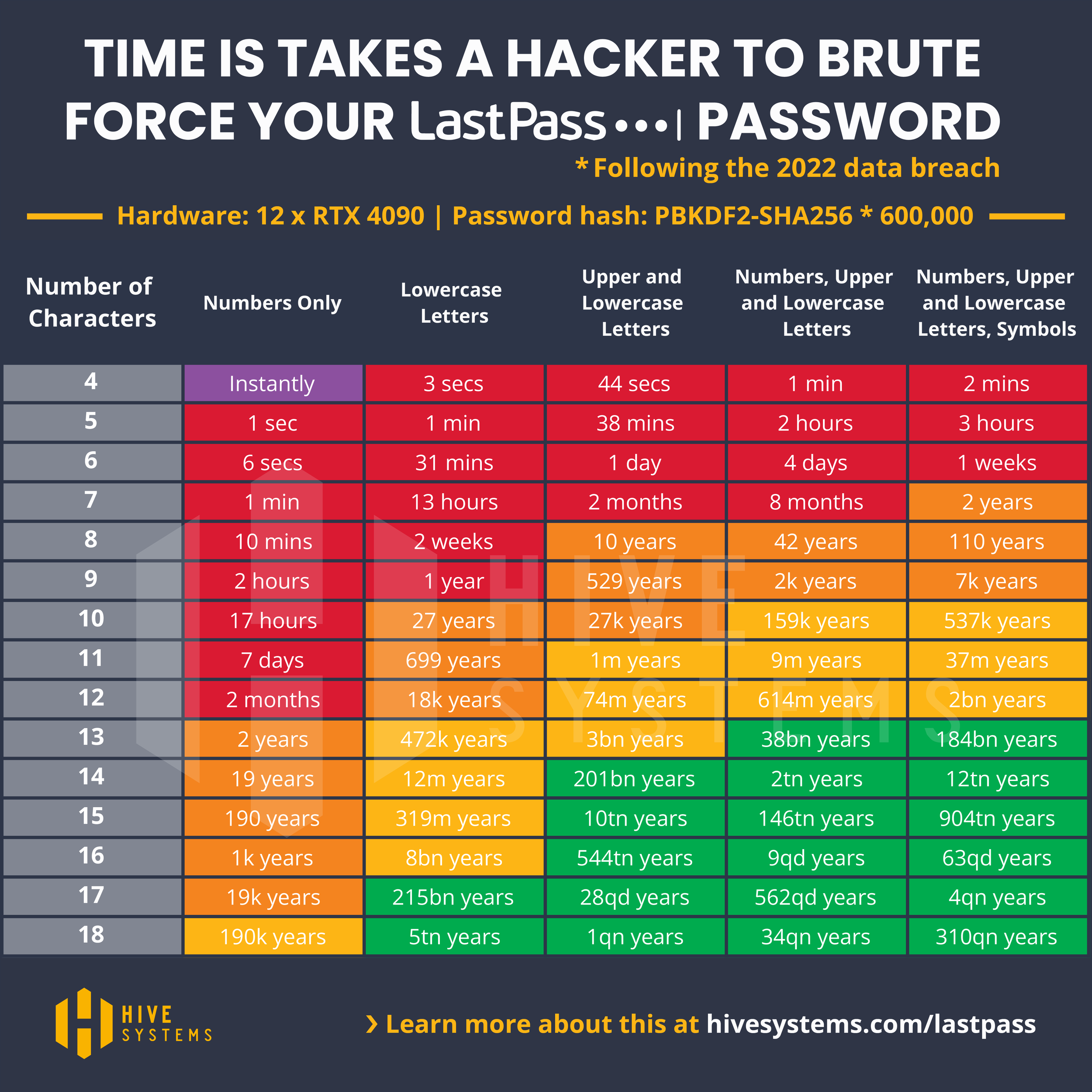
Examining the LastPass Breach Through our Password Table
The recent LastPass breach has been rattling around in the news and some researchers believe hackers may have begun to crack some of the stolen passwords. We generated another version of our famous password table for this scenario - read on!
Are Your Passwords in the Green in 2023?
We’ve updated our viral Hive Systems Password Table for 2023 and the industry-standard requirements are no longer secure! See why our Password Table has been shared by the news, universities, and companies across the globe - download your copy now!
The Data Breach Perception Problem in 2022
The 2022 update to our research that compares how data breaches happened, what academia published, what the news covered, and what people Googled. So what’s new, what was our methodology, and what was surprising? Read on!
Crypto Cons Continue
Crypto cons are heating up! Your insecure #web3 project could cost you if you don't secure it properly.
Are Your Passwords in the Green in 2022?
In 2022, we updated our viral Hive Systems Password Table that’s been seen in the news and shared everywhere - and this time we brought the receipts for the methodology behind our update!
These Passwords Are a Joke
If you’re the kind of person whose luggage combination is 1234, then you probably have a few of these passwords. It’s time to change.
What Really Caused Data Breaches in 2020?
Verizon’s 2021 Data Breach Investigations Report (DBIR) found that over 99% of all incident and breach events fall into one of only eight major categories. But we were interested in comparing what DBIR, Google, news outlets, and academia reported as the causes of those data breaches and the results were surprising.
A Lifetime of Training for Just One Email
Employee training is the most effective method of reducing your company's susceptibility to phishing attacks. How confident are you that your coworkers know how to recognize and avoid a phishing scam? Learn more about ePHISHiency!
Get it Together, Twitter-verse
Only 2.3% of Twitter users have 2-Factor Authentication set up, and most of them are using texts to receive it. Learn more about safer methods, like authenticator apps and security keys from our Social Media Protection Guide
Yes, People Are Really Still Using These Versions of Windows…
No matter what version of Windows you use, PrintNightmare affects you! Learn about the latest patches, updates, and versions
Don’t Let Ransomware Corrupt Your Data Completely
So your data’s been held for ransom. You’ve paid the hackers or someone else to recover your data, only to find out it’s been corrupted. Now what? Well, you can prevent this from happening with layered protections, like segmented backups. Hive Systems is here to help.
Here's How People Keep Track of Their Passwords
65% of people memorize their most-used passwords - are you one of them? For Password Week, Hive Systems is going to be bringing you the best ways to keep your accounts safe and your data secure.
Paying the Ransom is No Guarantee
If you've been infected with ransomware, what do you do?
Pay the ransom? Try to find a backup of your data somewhere? The bad news: the results are not always guaranteed.
You’ve Got a Lot to Lose to Insider Threat
How much do you know about insider threat and how you can prevent it from shutting down your business entirely? Check out our recent video workshop on Protecting Your Honey from Insider Threat on our Hive Live platform.
The Snowball Effect of Security Flaw Remediation Costs
The later in the Security Development Life Cycle you wait to remediate a security flaw, the greater the initial cost will be magnified according to NIST. Catch it early by implementing a Secure Software Development Framework!
Are You Being Targeted by Hackers Because of Your Age?
Hackers are targeting certain age groups, and it's costing them hundreds of millions every year nationwide. Learn more about how you can protect yourself from threats like phishing and increase the strength of your passwords by subscribing to the ACT Digest!
It’s Time to ACT Against Cyber Crime
Here's how many complaints of internet crime the IC3 Division of the FBI has received each year since 2016 and how much it cost businesses and individuals just like you. It's time to ACT and lock down your data. Subscribe to the ACT digest today!