Better Late Than Never: Addressing NIST’s Updated Password Security Guidance
Category
Awareness, Compliance, Cybersecurity Fundamentals, FedRAMP, CMMC
Risk Level
NIST recently updated its decades-old password security guidance after years of scrutiny, skepticism, and flat-out ineffectiveness finally forced the agency to address practical security considerations and realistic threats while abandoning what many considered to be ineffective security theater.
“What changed, and what is NIST's updated password guidance and the role of password strength in 2024?”
In an ever-evolving digital landscape, cybersecurity professionals must constantly adapt to emerging threats and modernize their strategies for protecting sensitive data. One area where best practices have evolved significantly over the past twenty years is password security best practices. For decades, users have been forced to navigate overly complex password requirements and password management requirements imposed across every part of their digital lives, leading to frustration and, ultimately, weaker security around their use and safeguarding of the critical secrets that protect their digital treasure troves of information. In response to this, after analyzing years of human behavior when it comes to password hygiene, the National Institute of Standards and Technology (NIST) issued updated guidance in its Special Publication 800-63B: Digital Identity Guidelines, fundamentally altering how organizations and users should approach password security and management.
For those who don’t know, NIST is a U.S. government agency whose mission is to develop technical and scientific standards primarily applicable to the government. These standards often extend beyond government via regulatory policies and law imposed on private sector industry and businesses. Since NIST consistently researches, publishes, and updates guidance and standards across a number of industry applications, many private sector organizations have adopted their standards as best practices where other frameworks or guidance are less robust or don’t exist. In the realm of cybersecurity, NIST publishes some of the most comprehensive frameworks, standards, and general guidance making it one of the ”go to” sources for CISOs to model their information security and privacy practices on, whether they are required to for various compliance obligations or not.
Let's take a closer look at the updated NIST guidance and explore why it matters for both cybersecurity professionals and everyday users. Additionally, we’ll take a look at how these changes gel with the findings in Hive Systems' famous password table to illustrate just how important strong, secure passwords are in today's threat environment.
“What are the key takeaways from NIST's updated password guidance?”
NIST’s updated recommendations represent a shift toward user-friendly security practices without compromising strength or reliability. NIST realized that burdening users with overly complex password composition schemes and rotation/change requirements, especially while newer security paradigms like Multi-Factor Authentication or Passwordless Auth exist to mitigate the risks of weak passwords, only resulted in weaker password selection, weaker password safeguarding, and a higher likelihood of reuse of the same, poorly constructed passwords across many services a user might use on a day-to-day basis.
Additionally, NIST researchers identified that most password-based attacks do not occur via online brute forcing or password guessing, but rather “offline” cracking against those hashes (the encrypted format of a password stored by a service) that were compromised from a service provider using specific, common patterns or information derived about a target from publicly available information. Attackers usually then leveraged these cracked passwords in what are commonly referred to as “credential stuffing attacks” where they try a combination of the cracked passwords with email addresses or user IDs also previously stolen across many services to see if a) an account exists in the service and b) if any of the passwords they successfully cracked work for that account. Attackers move service by service starting with things like email providers, social media services, banking and finance services, etc. to see where credentials may be reused and relied upon solely to gain access.
So, how did NIST address these concerns exactly?
1. Prioritize Length Over Complexity
NIST now advises that password length is more critical than complexity. For years, users were forced to create complex passwords containing a mix of uppercase letters, numbers, and special characters. The new guidelines suggest a minimum password length of 8 characters, but for more sensitive accounts, it’s recommended to use passwords between 12 and 64 characters.
This shift aims to promote the use of passphrases — easy-to-remember yet long combinations of words, which provide enhanced security over shorter, complex passwords that users might struggle to recall. An example of a strong passphrase may be a combination of words that only you may understand the relevance of (ex. “Angry-Cats-Want-Treats!”) and is not easily discernible from your digital footprint (avoiding things like childrens’ or family member names, the street names you’ve lived on, or other Google-able facts). Adding a few capital letters or a special character here or there is helpful if you are worried about an attacker using advanced techniques to iterate through permutations and combinations of dictionary words.
2. No More Forced Periodic Changes
Gone are the days of being required to change your password every 60 or 90 days. NIST’s new guidance discourages forcing periodic password resets unless there is evidence of a breach or compromise. The reasoning here is simple: when users are forced to change passwords frequently, they tend to create simpler passwords or simply make minor modifications to existing ones (e.g., "password1" becomes "password2"). As a user, you may not always be notified timely of suspected breaches, so if you have any indication your password has been compromised, especially if you are reusing it across services, you should still change it immediately.
3. Eliminate Arbitrary Complexity Rules
The updated guidance encourages systems to avoid imposing strict rules, such as mandating the inclusion of special characters, numbers, and mixed cases. While these can help improve security, they often lead users to create predictable patterns, undermining their effectiveness. Instead, longer passwords or passphrases provide better defense. Additionally, most organizations or services tend to restrict which special characters can be used and publish that information in password help text when they force you to create a password which helps attackers hone in on which characters the user may have selected from. Besides, most users commonly select a symbol at the end (and usually “!” or “?”) or, in lieu of a letter, use “1337 5p34k” (leet speak). Attackers know this and use methods to reduce the set of possible passwords when they are cracking them offline to target these “known” or “common” uses.
4. Disallow Common and Compromised Passwords
NIST recommends organizations implement screening measures to prevent the use of easily guessable passwords or those known to have been compromised in previous data breaches. This includes avoiding commonly used passwords like "password123" and checking against known breached passwords available in databases.
Beyond common or compromised passwords, users should always avoid reusing any passwords across services. A long, strong password is only as safe and secure as the weakest security it is stored with. If passwords are reused between secure services (banking, healthcare) and insecure services (internet forums, casual websites) and one of those insecure services is breached and they weren’t storing your password in a properly secure manner, guess what… every other service you used that password for is now effectively compromised. Nothing like having your bank accounts drained because you only had password-based access on those accounts AND you used the same email and password combination to sign up for a gardening club website that stored your password unencrypted and ultimately got breached by a 16 year-old script kiddie living half-way across the world.
5. Use of Multi-Factor Authentication (MFA) and Password Managers
NIST strongly advocates for the use of multi-factor authentication (MFA), which adds an additional layer of security by requiring users to provide a second form of authentication beyond just a password. For more information on MFA, check out our blog post A Beginner's Guide to 2FA and MFA.
Additionally, password managers are recommended to store long and complex passwords securely without requiring users to remember them.
Password managers are not a panacea, and certainly introduce unique risks and challenges themselves, but those risks are generally more palatable than those facing most users who have weak password security and management practices out of convenience. Most reputable password managers like Bitwarden, 1Password, Last Pass, Apple Password Manager, or Chrome Password Manager integrate securely and efficiently with Chrome, Firefox, Brave, and Edge, have some operating system level support, and mobile application and browser support for portability and ease of use. For more information on selecting and using password managers see our blog post How Am I Supposed to Remember All These Passwords?
6. No Knowledge-Based Authentication Questions
Knowledge-based authentication questions (e.g., "What’s your mother's maiden name?") are discouraged because many answers to these questions can easily be discovered through social media or public records. Instead, stronger authentication methods like biometrics or MFA are preferred.
7. Throttling Login Attempts
Rather than locking an account after a set number of failed login attempts, which can be exploited by attackers to deny access, NIST recommends throttling login attempts. This approach slows down the response time after multiple failed logins, frustrating automated online attack tools without locking legitimate users out.
”So, how strong should passwords be anyway?”
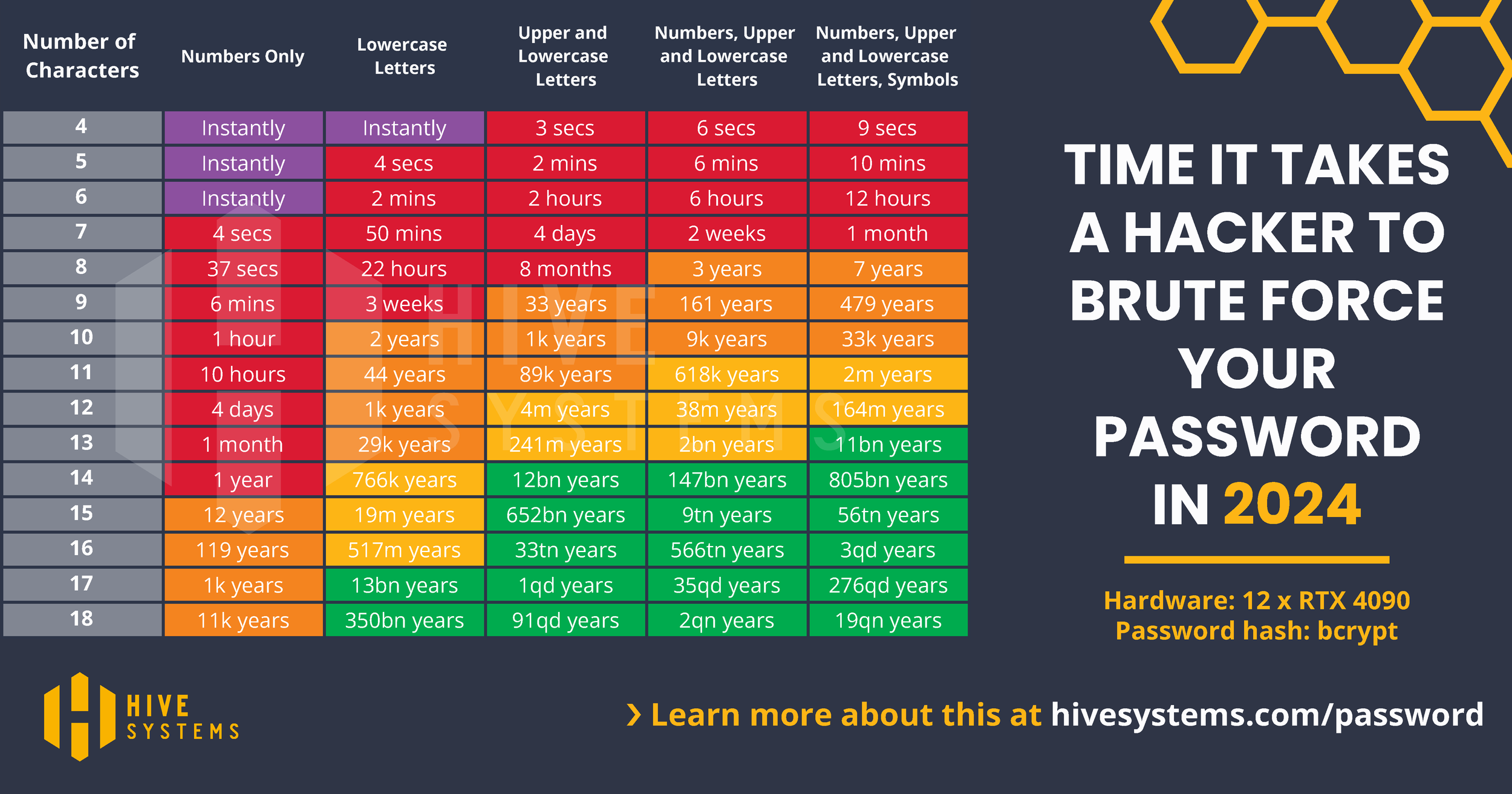
To better understand the implications of NIST’s recommendations, it’s important to evaluate how quickly different passwords can be cracked using modern computing power. Hive Systems recently updated its widely referenced password-cracking table for 2024, which shows how long it would take to crack various password lengths and types if the secure hashes (encrypted format) of those passwords were stolen by attackers.
Download our Password Table here: https://www.hivesystems.com/blog/are-your-passwords-in-the-green
As you can see from the table, a 12-character password using numbers, uppercase and lowercase letters, and symbols can take centuries to crack using current technology. However, a shorter or less complex password might be cracked in mere seconds. This coincides with NISTs focus on the “longer is better” approach, and messaging highlights the importance of both password length and a diverse character set, especially when MFA isn’t in use.
The updated table shows that while longer passwords are generally more secure, passwords composed of common phrases or predictable patterns can still be vulnerable to brute-force or dictionary attacks, once again echoing NIST’s guidance against using common or easily guessed/discerned information to create your passwords. Thus, using a password manager to generate and store truly random and lengthy passwords or passphrases is a critical strategy for maintaining strong password hygiene.
“What are some practical steps for implementing NIST’s updated guidance?”
Organizations looking to update their password policies in line with NIST’s recommendations can take several practical steps:
Encourage the use of passphrases: Instead of complex, hard-to-remember passwords, suggest users adopt longer passphrases that are easier to retain and more secure.
Implement password deny lists: Use tools that screen against known compromised and common passwords, preventing their use.
Promote MFA: Push for the adoption of multi-factor authentication across all sensitive systems, significantly reducing the risk posed by compromised passwords.
Offer password manager tools: Provide employees and users with access to secure password managers, which simplify the process of generating and storing strong passwords.
By following these guidelines and staying aware of evolving threats, organizations can strike the perfect balance between usability and security, ensuring that their systems and data remain protected in an increasingly hostile cybersecurity environment.
The future of password security: Hive Systems will get you there
NIST’s updated guidance represents a pragmatic approach to password security. By focusing on longer, more user-friendly passwords and eliminating outdated practices like periodic password resets and arbitrary complexity rules, NIST aims to reduce friction while strengthening overall security. Coupled with tools like Hive Systems' updated password strength table, it’s clear that robust, secure password management is achievable for both individuals and organizations.
As we continue into 2024, ensuring that your organization’s password policies are up-to-date and aligned with NIST’s guidance is more critical than ever. Embracing these recommendations will not only make security stronger but also help to reduce user fatigue and encourage better password hygiene across the board.
Hive Systems’ team of experts can help your organization with all of its password security needs from policy development and roll out, to technical solutions and workforce password security training. Reach out to Hive Systems and let us know how we can help you!
Follow us - stay ahead.