Low-Cost Security for Small Businesses
Cybersecurity doesn’t have to be expensive—affordable training and free government resources can go a long way in protecting your business from human error, the root of most cyber incidents.
Think You Can Spot a Phishing Scam? Think Again.
Phishing emails are getting harder to detect. Even the savviest professionals can fall victim. Learn how to test your team’s awareness and keep your organization secure.
Government Proposes New CUI Rules for all Federal Contractors
If you work with Controlled Unclassified Information (CUI), the new proposed rule implements new requirements, including NIST 800-171 revision 2 compliance, for all federal contractors. Read our article to see how this could impact your company in the coming years.
Getting Ahead of CMMC with Joint Surveillance Voluntary Assessments
A JSVA could be the answer your company has been looking for to get ahead of CMMC. Katie, a CCA on our team, helps outline everything you need to know about getting CMMC Level 2 certified - giving your company the advantage before CMMC even starts!
Better Late Than Never: Addressing NIST’s Updated Password Security Guidance
NIST recently updated its decades-old password security guidance after years of scrutiny, skepticism, and flat-out ineffectiveness finally forced the agency to address practical security considerations and realistic threats while abandoning what many considered to be ineffective security theater.
A Farewell to the JAB
The Federal Risk and Authorization Management Program (FedRAMP) has been a cornerstone for ensuring the security of cloud services used by federal agencies. Recently, significant changes to the program - specifically the sunset of the JAB have sparked discussions across the cloud computing landscape.
Navigating the Dual Impact of AI in Cybersecurity
Artificial Intelligence (AI) is set to be the newest ally for many companies, but it’s also set to be the newest threat.
SOC 2 Made Simple
Are you tired of filling out lengthy vendor questionnaires and are looking to pursue an SOC 2 examination report instead? Discover some basic practices to secure your customers’ data and pave the way for SOC 2 certification.
On Your DMARC, Get Set, Go!
Google and Yahoo are requiring DMARC beginning in February 2024. So what does that mean for your organization, and how do you implement it?
Who is Watching You and Why?
In the musical words of Rockwell, 🎵 “I always feel like somebody’s watching me - and I have no privacy.” 🎵Who might be watching you through your webcam, and what can you do to stop it?
Deepfakes: Can You Trust What You See?
With hackers having easy access to AI, we can never be sure whether what we are seeing is true or not. We live in an age where information can be easily manipulated so it is critical to learn how to identify and counter these fakes.
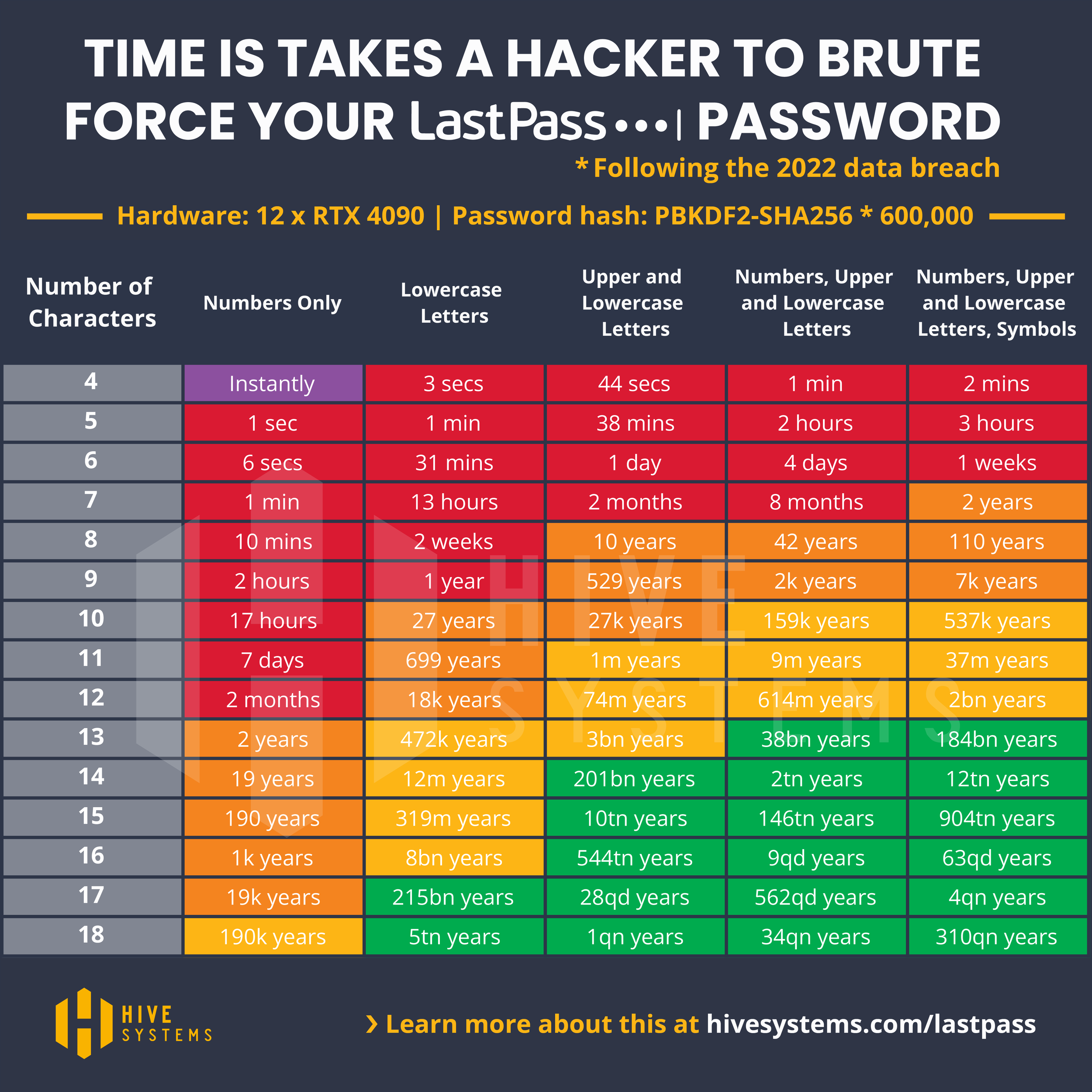
Examining the LastPass Breach Through our Password Table
The recent LastPass breach has been rattling around in the news and some researchers believe hackers may have begun to crack some of the stolen passwords. We generated another version of our famous password table for this scenario - read on!
Brand New SEC Cybersecurity Requirements
The new requirements are meant to keep investors apprised of the cybersecurity risks taken by public companies. That includes both your current state as well as any ongoing or future incidents that will need to be evaluated for materiality and then reported within a 4 day period.
HTTPS is Secure (Except When it’s Not)
This may be an unpopular opinion: HTTPS is not secure, or at least not always. Let’s go back in time to review what HTTP and HTTPS are and are not - and some of the ways you can protect yourself online.
Exploring Human Errors in Cybersecurity
You may have thought that hackers wore black suits and rappelled off the roof to hack a company, but that only exists in Hollywood. In real life, human error remains one of the leading causes of cybersecurity breaches.
Data Breach 101: Actions to Take After a Breach
Data breaches are a significant concern here in the digital age. With technology advancing rapidly, hackers have been using various methods to gain sensitive information from unsuspecting individuals, organizations, and you.
#Secure: Locking Down Your Social Media in Style
Social media platforms are essential tools for personal and professional communication. The increasing number of cyber threats means protecting your accounts has become paramount.
Telecommunications: A Case Study
As one of the world’s fastest-growing industries, telecommunication has become a highly vulnerable target for cybersecurity threats. We explore the reasons why.
Keep Calm and Check Your Public Wi-Fi Connection
When it comes to public Wi-Fi, it is “better to be safe than sorry.” Read our guide and secure your Wi-Fi connection when you travel.
Let’s Not Get Smished
Email isn't the only way hackers try to get your information. They can also use text messages to entice victims to click on links in scams known as “smishing.”