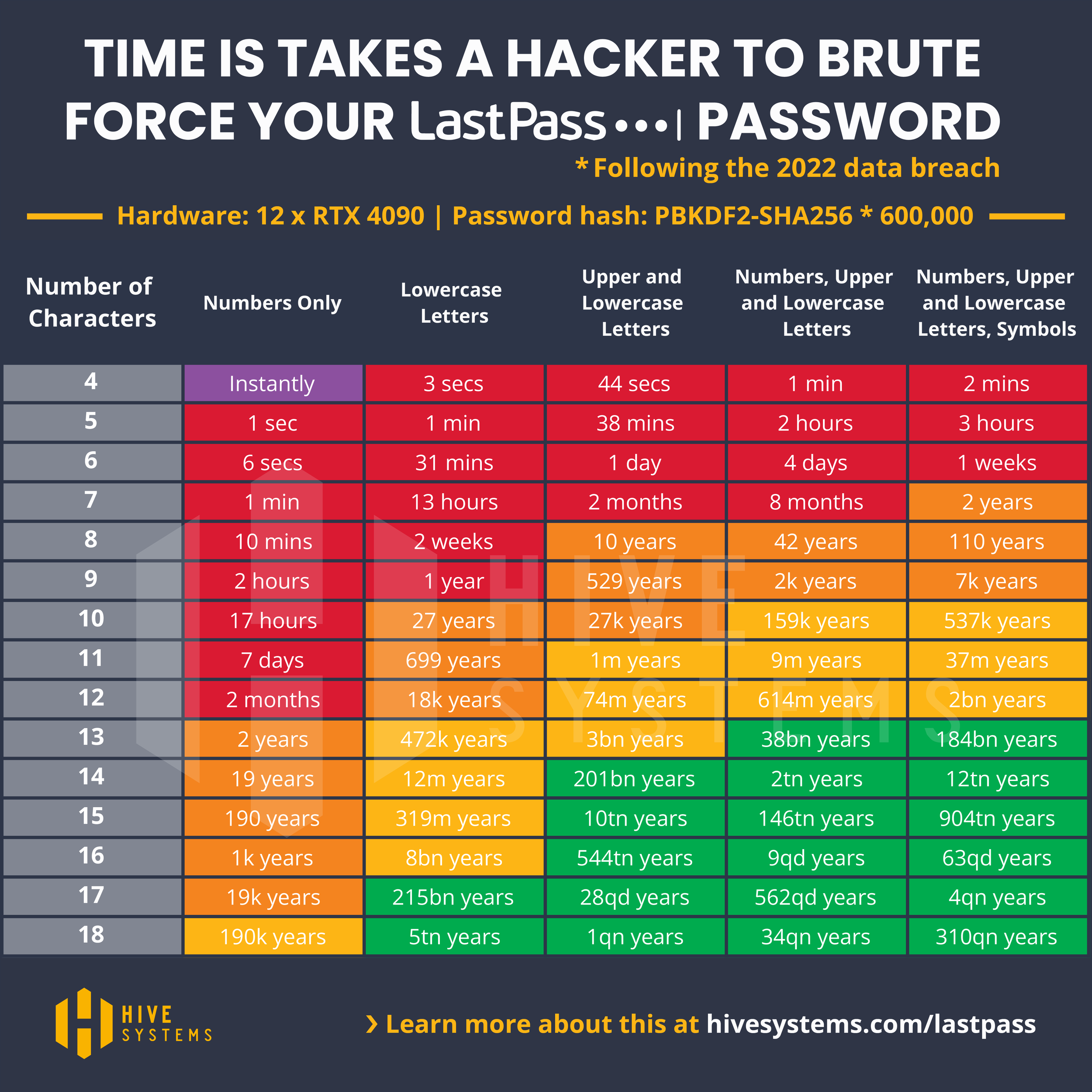
Examining the LastPass Breach Through our Password Table
The recent LastPass breach has been rattling around in the news and some researchers believe hackers may have begun to crack some of the stolen passwords. We generated another version of our famous password table for this scenario - read on!
Passkey to the (Passwordless) Future
What would it be like to live in a world without having to memorize and type a million of passwords? Logging in without having to enter a password has been practically impossible - until now.
Brand New SEC Cybersecurity Requirements
The new requirements are meant to keep investors apprised of the cybersecurity risks taken by public companies. That includes both your current state as well as any ongoing or future incidents that will need to be evaluated for materiality and then reported within a 4 day period.
HTTPS is Secure (Except When it’s Not)
This may be an unpopular opinion: HTTPS is not secure, or at least not always. Let’s go back in time to review what HTTP and HTTPS are and are not - and some of the ways you can protect yourself online.
Exploring Human Errors in Cybersecurity
You may have thought that hackers wore black suits and rappelled off the roof to hack a company, but that only exists in Hollywood. In real life, human error remains one of the leading causes of cybersecurity breaches.
Newly Exploited Vulnerabilities in Apple Devices
In mid-April, the Cybersecurity and Infrastructure Agency (CISA) ordered federal agencies to patch two vulnerabilities actively being exploited on iOS, iPadOS, and macOS devices. The vulnerabilities were also added to CISA’s Known Exploited Vulnerabilities catalog as of April 10th.
Are Your Passwords in the Green in 2023?
We’ve updated our viral Hive Systems Password Table for 2023 and the industry-standard requirements are no longer secure! See why our Password Table has been shared by the news, universities, and companies across the globe - download your copy now!
Data Breach 101: Actions to Take After a Breach
Data breaches are a significant concern here in the digital age. With technology advancing rapidly, hackers have been using various methods to gain sensitive information from unsuspecting individuals, organizations, and you.
#Secure: Locking Down Your Social Media in Style
Social media platforms are essential tools for personal and professional communication. The increasing number of cyber threats means protecting your accounts has become paramount.
Telecommunications: A Case Study
As one of the world’s fastest-growing industries, telecommunication has become a highly vulnerable target for cybersecurity threats. We explore the reasons why.
I’m Sorry, But That’s Classified
The discovery of classified information at high profile politicians’ homes and alternate work locations has seemingly swarmed the news cycle in the past six months. Let’s take a look at what classified information is and how it is managed by the United States government.
Digital Banking - Case Study
Banks are taking revolutionary approaches to digitize and streamline the customer experience - but these measures could come with a cost without strategic cybersecurity measures.
Hospital & Healthcare Technology - Case Study
The healthcare industry is facing an onslaught of ever-growing cyber threats. Read our case study on the industry’s vulnerabilities and how you can help your company stay ahead of hackers.
Keep Calm and Check Your Public Wi-Fi Connection
When it comes to public Wi-Fi, it is “better to be safe than sorry.” Read our guide and secure your Wi-Fi connection when you travel.
Let’s Not Get Smished
Email isn't the only way hackers try to get your information. They can also use text messages to entice victims to click on links in scams known as “smishing.”
The Data Breach Perception Problem in 2022
The 2022 update to our research that compares how data breaches happened, what academia published, what the news covered, and what people Googled. So what’s new, what was our methodology, and what was surprising? Read on!
Black Friday and Cyber Monday Cyber Scams on the Rise
Holiday shopping season is upon us, but it may not be so jolly if you take risks when shopping online. Read our guide for how to stay safe when shopping for gifts this year!
September Snafus: Hackers Take Advantage of Unwitting Employees
Several large companies were hacked in the first half of September. The common theme? All of the attacks were carried out with relatively simple phishing and social engineering techniques.
Crypto Cons Continue
Crypto cons are heating up! Your insecure #web3 project could cost you if you don't secure it properly.
I am once again asking you to update your Apple devices
Apple has released critical fixes for critical problems on its devices - so spend ten minutes and update them now!