Are Your Passwords in the Green?
It's the 2024 update to our Hive Systems Password Table - including using a new “most-hacked” password hash. See why our Password Table has been shown and written about on the news, published by universities, and shared by companies across the globe. Learn more and download your copy!
Let’s Talk About Cookies!
Cookies help enhance our browsing experience, but what are the risks? Learn more about how cookies work, what data they collect, and how you can protect your data from misuse.
Navigating the Dual Impact of AI in Cybersecurity
Artificial Intelligence (AI) is set to be the newest ally for many companies, but it’s also set to be the newest threat.
SOC 2 Made Simple
Are you tired of filling out lengthy vendor questionnaires and are looking to pursue an SOC 2 examination report instead? Discover some basic practices to secure your customers’ data and pave the way for SOC 2 certification.
On Your DMARC, Get Set, Go!
Google and Yahoo are requiring DMARC beginning in February 2024. So what does that mean for your organization, and how do you implement it?
The Race to CMMC Compliance: Understanding the DoD’s New Implementation Plan
The DoD just released a proposed rule for implementation of all CMMC requirements by October 1, 2026. The plan will be implemented in four phases.
The Weakest Link: Managing Supply Chain Risk
In the interconnected web of modern business ecosystems, supply chain risks have emerged as insidious threats, leaving even the most vigilant organizations vulnerable to devastating cyber breaches.
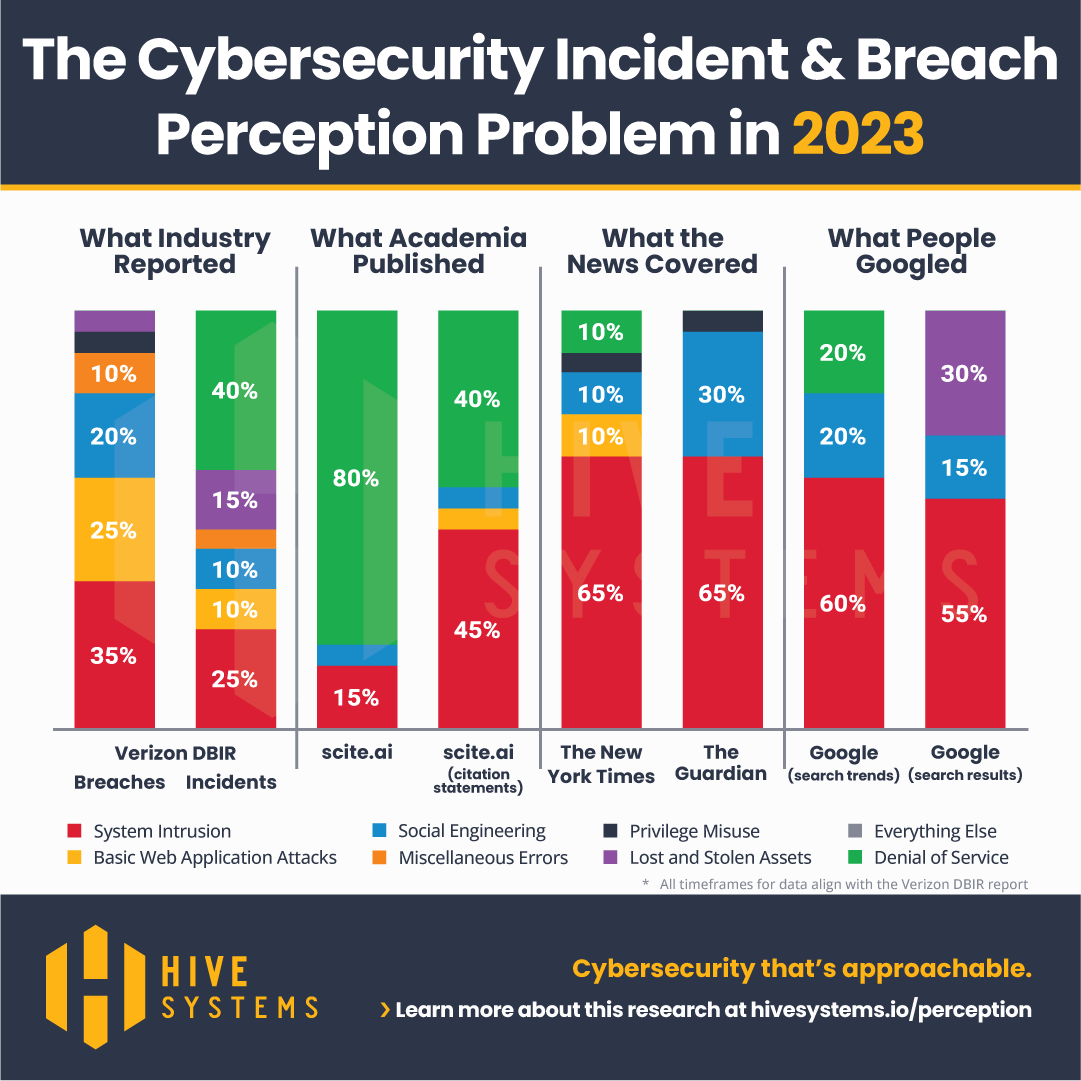
The Cyber Attack Perception Problem in 2023
The 2023 update to our research that compares how cybersecurity incidents and data breaches occurred, what academia published, what the news covered, and what people Googled. So what’s new this year, what was our methodology, and what was surprising? Read on!
Approachable CMMC: Accelerate with our SSP Template
Are you part of the Defense Industrial Base (DIB) or have Department of Defense (DoD) contracts? Then your deadline for implementing the Cybersecurity Maturity Model Certification (CMMC) 2.0 requirements is fast approaching.
Who is Watching You and Why?
In the musical words of Rockwell, 🎵 “I always feel like somebody’s watching me - and I have no privacy.” 🎵Who might be watching you through your webcam, and what can you do to stop it?
Deepfakes: Can You Trust What You See?
With hackers having easy access to AI, we can never be sure whether what we are seeing is true or not. We live in an age where information can be easily manipulated so it is critical to learn how to identify and counter these fakes.
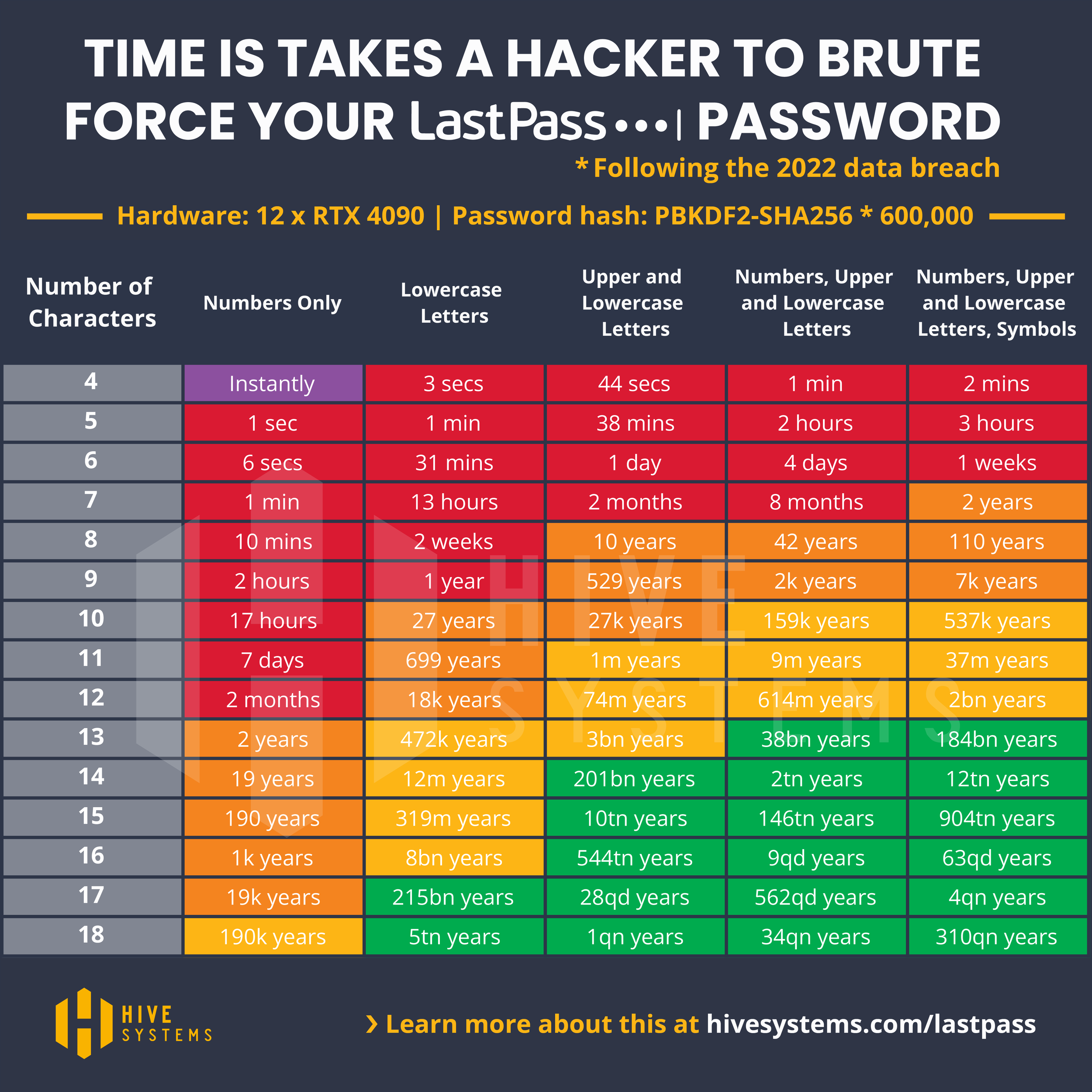
Examining the LastPass Breach Through our Password Table
The recent LastPass breach has been rattling around in the news and some researchers believe hackers may have begun to crack some of the stolen passwords. We generated another version of our famous password table for this scenario - read on!
Passkey to the (Passwordless) Future
What would it be like to live in a world without having to memorize and type a million of passwords? Logging in without having to enter a password has been practically impossible - until now.
Brand New SEC Cybersecurity Requirements
The new requirements are meant to keep investors apprised of the cybersecurity risks taken by public companies. That includes both your current state as well as any ongoing or future incidents that will need to be evaluated for materiality and then reported within a 4 day period.
HTTPS is Secure (Except When it’s Not)
This may be an unpopular opinion: HTTPS is not secure, or at least not always. Let’s go back in time to review what HTTP and HTTPS are and are not - and some of the ways you can protect yourself online.
Exploring Human Errors in Cybersecurity
You may have thought that hackers wore black suits and rappelled off the roof to hack a company, but that only exists in Hollywood. In real life, human error remains one of the leading causes of cybersecurity breaches.
Newly Exploited Vulnerabilities in Apple Devices
In mid-April, the Cybersecurity and Infrastructure Agency (CISA) ordered federal agencies to patch two vulnerabilities actively being exploited on iOS, iPadOS, and macOS devices. The vulnerabilities were also added to CISA’s Known Exploited Vulnerabilities catalog as of April 10th.
Are Your Passwords in the Green in 2023?
We’ve updated our viral Hive Systems Password Table for 2023 and the industry-standard requirements are no longer secure! See why our Password Table has been shared by the news, universities, and companies across the globe - download your copy now!
Data Breach 101: Actions to Take After a Breach
Data breaches are a significant concern here in the digital age. With technology advancing rapidly, hackers have been using various methods to gain sensitive information from unsuspecting individuals, organizations, and you.
#Secure: Locking Down Your Social Media in Style
Social media platforms are essential tools for personal and professional communication. The increasing number of cyber threats means protecting your accounts has become paramount.