FedRAMP 20x: Change is Coming, But Are We Ready?
The federal government is overhauling FedRAMP under the bold FedRAMP 20x initiative. For cloud service providers, this is the time to shape the future—not watch from the sidelines. Hive Systems explains what’s changing, why it matters, and how security pros can lead the charge.
Financial Fallout: The True Cost of Employee Loss
When thousands of workers are laid off at once, it's not just jobs that disappear, and the technical and financial ripple effects reach every corner of the country.
Preparing a Cryptographic Inventory for a Post Quantum Computing World
Quantum threats are real - and your cryptographic assets are at risk. QrytpoCyber, one of our leading products, shows why creating a full cryptographic inventory is step one in futureproofing your organization’s cybersecurity. Watch the video to see how we’re solving one of cybersecurity’s most complex challenges.
This Major Vulnerability Could Fill Your Computer with Bees (Seriously)
A newly discovered vulnerability lets attackers swarm your system with thousands of virtual bees — and yes, it’s as wild (and dangerous) as it sounds. Hive Systems breaks down the real security flaw behind the buzz and what it means for defenders.
Low-Cost Security for Small Businesses
Cybersecurity doesn’t have to be expensive—affordable training and free government resources can go a long way in protecting your business from human error, the root of most cyber incidents.
Silk Typhoon: Unmasking the Cyber Espionage Threat Targeting the U.S. Supply Chain
Hackers are setting their sights on the IT supply chain, and your data is the prize. Meet Silk Typhoon—the latest cyber threat you need to know about.
Think You Can Spot a Phishing Scam? Think Again.
Phishing emails are getting harder to detect. Even the savviest professionals can fall victim. Learn how to test your team’s awareness and keep your organization secure.
Government Proposes New CUI Rules for all Federal Contractors
If you work with Controlled Unclassified Information (CUI), the new proposed rule implements new requirements, including NIST 800-171 revision 2 compliance, for all federal contractors. Read our article to see how this could impact your company in the coming years.
Your Guide to Engaging with a C3PAO
CMMC is here and C3PAO assessments began on January 2, 2025. So what should you expect from an assessment, and how can you set your company up for success?
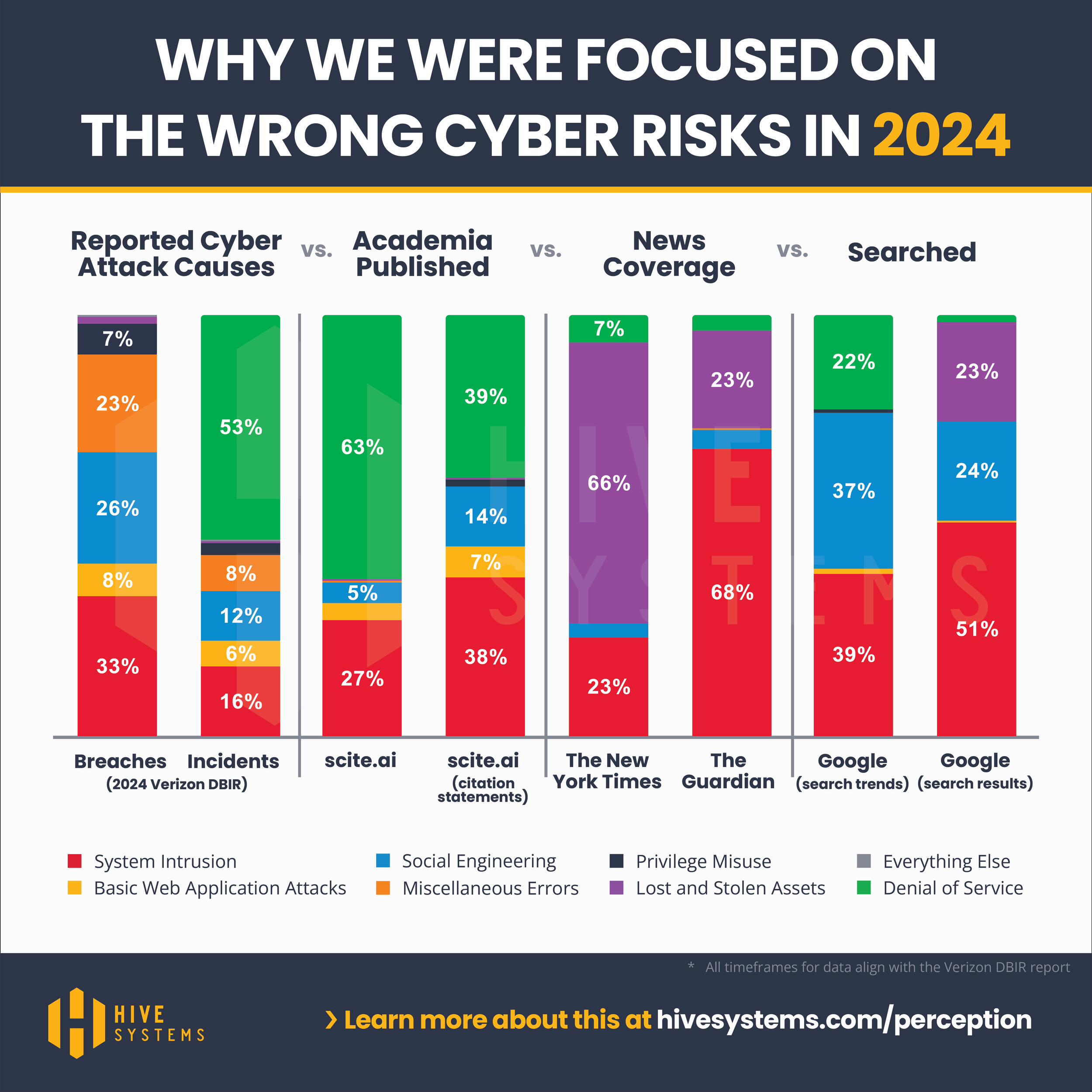
The Cyber Attack Perception Problem
Uncover the truth about cyber attack misconceptions with Hive Systems' latest research. Learn how media coverage skews public perception of cyber attacks and discover the real risks organizations face. Explore data-driven insights to better protect your business in an evolving threat landscape
CMMC Is Here: Your Essential Guide to Identifying and Protecting Federal Contract Information (FCI)
As the CMMC program takes effect, understanding what qualifies as Federal Contract Information (FCI) is critical. This guide breaks down FCI definitions, offers practical tips for identifying and handling FCI across your organization, and walks you through applying CMMC Level 1 controls—ensuring you stay compliant, secure, and ready for the new era of defense contracting.
Ready, Set, Respond! Planning an Effective Incident Response Strategy.
Dwight D. Eisenhower, the 34th U.S. president, once said, 'Plans are nothing; planning is everything.' In this post we’ll dive into the fundamentals of incident response planning, and take it a step further to show how planning for an incident goes beyond just documentation.
Getting Ahead of CMMC with Joint Surveillance Voluntary Assessments
A JSVA could be the answer your company has been looking for to get ahead of CMMC. Katie, a CCA on our team, helps outline everything you need to know about getting CMMC Level 2 certified - giving your company the advantage before CMMC even starts!
RED ALERT: CMMC Begins December 16th
The long-awaited CMMC rule has finally been officially published and is accompanied by some beneficial changes from the original draft. We break them down for you so you and your organization can begin to prepare for the imminent enforcement.
Better Late Than Never: Addressing NIST’s Updated Password Security Guidance
NIST recently updated its decades-old password security guidance after years of scrutiny, skepticism, and flat-out ineffectiveness finally forced the agency to address practical security considerations and realistic threats while abandoning what many considered to be ineffective security theater.
A Farewell to the JAB
The Federal Risk and Authorization Management Program (FedRAMP) has been a cornerstone for ensuring the security of cloud services used by federal agencies. Recently, significant changes to the program - specifically the sunset of the JAB have sparked discussions across the cloud computing landscape.
It’s Time For Your Wakeup Call: CMMC is Almost Here!
CMMC has been on the horizon for years, lurking in the distance and often thought of as a “tomorrow” problem. With the publication of the proposed rule to amend DFARS 252.204-7021, let this be a wake up call: CMMC is coming - and it’s coming quickly.
BEWARE: Job scams are on the rise!
Job scams are on the rise and they’re coming straight to your phone via text, email, and even social media. Watch this interview with our CEO, Alex Nette, who explores the ways to identify a job scam and stay ahead of scammers if you’re on the hunt for a job!
Breach Confirmed! Change Healthcare Cyber Event to Impact Millions
Change Healthcare, owned by healthcare giant UnitedHealth Group, has confirmed that patient data was exfiltrated from their environment after all - a stunning reveal that will impact millions of patient records.
NIST Releases New CUI Security Requirements
The long-awaited NIST 800-171 Revision 3 has been released. What’s new, and what are the implications for CMMC?